Internet Security and Privacy
Our research group has been developing data-driven approaches to security and privacy, with a focus on applying machine learning to Internet-based attacks. The group has developed technology that was the basis for many breakthrough innovations in Internet security and privacy, including:
- the first spam filtering system based on network-level features (SNARE);
- the first botnet detection startup based on DNS queries (Damballa)
- the first early warning system using DNS registration information to detect early warning (Predator)
- the first large-scale study of security and privacy vulnerabilities of smart home Internet of Things (IoT) devices (IoT Inspector)
Our research has resulted in transition to practice, through startup companies, integration into existing products, collaborations with industry through joint intellectual property agreements, and advisories to regulatory and other government agencies (e.g., the Federal Trade Commission).
Recently, we have been applying machine learning to detect outliers and anomalies in smart home Internet of Things (IoT) traffic, and applying machine learning to automatically learn normal (and outlier) behavior of IoT traffic, with applications to smart homes, smart cities, and smart infrastructure.
We are also performing research in the area of DNS privacy, designing protocols and systems to improve the privacy properties of DNS.
IoT Security and Privacy
The Internet Of Things (IoT) market is predicted to grow at $520B in valuation by 2021, more than double the $235B spent in 2017, according to Forbes. The increasing popularity of these "smart" IoT consumer devices raises many interesting research questions. We have replicated a residential broadband Internet network inside an experimental laboratory to study security, privacy, and network performance. By hosting several IoT devices (powered by CableLabs), we provide a unique opportunity for you to experiment with new and existing datasets, apply data science and machine learning techniques to uncover new insights and valuable information, or build your new application or research project.
The Internet of Things (IoT) lab at the Center for Data and Computing at the University of Chicago is a unique resource that allows us to explore the security and privacy behaviors of a wide variety of devices. For example, some of our recent work has explored the tracking behavior of Smart TVs.
DNS Privacy
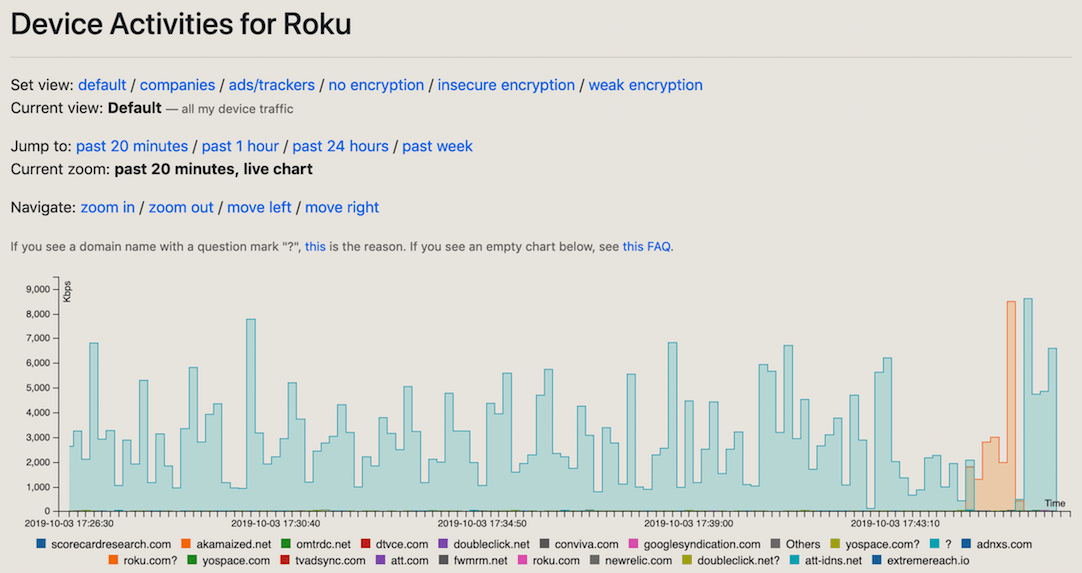
DNS reveals information that an Internet user may want to keep private, such as websites, user identifiers, MAC addresses, and IP subnets. This information can be visible to a third party or even between a recursive resolver and an authoritative server. Yet, even existing solutions such as DNS Query Name Minimization, DNS-over-HTTPS (DoH), and DNS-over-TLS (DoT) do not completely protect Specifically, prevent DNS operators from learning information which domains specific users are interested in. We are developing various technologies that work in conjunction with encrypted DNS solutions to further protect user privacy in these settings.
Distributed DNS (DDNS) revisit the trend towards centralized DNS and explores re-decentralizing the DNS such that clients might use multiple DNS resolvers when resolving domain names. We propose and evaluate several candidate decentralized architectures, laying the groundwork for future research to explore decentralized, encrypted DNS architectures that strike a balance between privacy and performance.
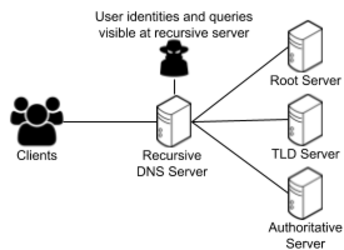
Oblivious DNS (ODNS) aims to protect user privacy against a powerful adversary that has the capabilities to: 1) eavesdrop on communications between clients and recursive resolvers, and between recursive resolvers and authoritative name servers, 2) request data (via subpoena/warrant) from any number of DNS operators, 3) maliciously access data at any DNS server.
Selected Publications
-
IoT Inspector: Crowdsourcing Labeled Network Traffic from Smart Home Devices at Scale
Danny Yuxing. Huang, Noah Apthorpe, Gunes Acar, Frank Li, and Nick Feamster.
Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies (IMWUT / Ubicomp). 2020.
-
Watching You Watch: The Tracking Ecosystem of Over-the-Top TV
Streaming Devices
Hooman Mohajeri Moghaddam, Gunes Acar, Ben Burgess, Arunesh Mathur, Danny Yuxing Huang, Nick Feamster, Edward W. Felten, Prateek Mittal, Arvind Narayanan.
ACM Conference on Computer and Communications Security (CCS). 2019. -
Keeping the Smart Home Private with Smart(er) IoT Traffic Shaping
Noah Apthorpe, Danny Yuxing Huang, Dillon Reisman, Arvind Narayanan, Nick Feamster.
Privacy Enhancing Technologies Symposium (PETS). 2019. -
Evaluating the Contextual Integrity of Privacy Regulation: Parents' IoT Toy
Privacy Norms Versus COPPA
Noah Apthorpe, Sarah Varghese, Nick Feamster.
USENIX Security Symposium. 2019. -
Selling a Single Item with Negative Externalities (a case for IoT regulation)
Matheus Xavier Ferreira, Danny Yuxing Huang, Tithi Chattopadhyay, Nick Feamster, S. Matthew Weinberg.
International World Wide Web Conference (WWW). 2019. -
User Perceptions of Smart Home IoT Privacy
Serena Zheng, Noah Apthorpe, Marshini Chetty, Nick Feamster.
ACM Conference on Computer Supported Cooperative Work and Social Computing (CSCW). 2018. -
Fast Web-based Attacks to Discover and Control IoT Devices
Gunes Acar, Danny Y. Huang, Frank Li, Arvind Narayanan, and Nick Feamster.
ACM SIGCOMM Workshop on IoT Security and Privacy. 2018. -
Security and Privacy Analyses of Internet of Things Children's Toys
Gordon Chu, Noah Apthorpe, Nick Feamster.
IEEE Internet of Things Journal (IoT-J). 2018. -
Machine Learning DDoS Detection for Consumer Internet of Things Devices
Rohan Doshi, Noah Apthorpe, Nick Feamster.
IEEE Deep Learning and Security Workshop (DLS). 2018. -
Discovering IoT Smart Home Privacy Norms using Contextual Integrity
Noah Apthorpe, Yan Shvartzshnaider, Arunesh Mathur, Dillon Reisman, Nick Feamster.
ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies (Ubicomp/IMWUT). 2018. -
Cleartext Data Transmissions in Consumer IoT Medical Devices
Daniel Wood, Noah Apthorpe, Nick Feamster.
Workshop on Internet of Things Security and Privacy (IoT S&P). 2017 -
Closing the Blinds: Four Strategies for Protecting Smart Home Privacy from Network Observers
Noah Apthorpe, Dillon Reisman, Nick Feamster.
Workshop on Technology and Consumer Protection (ConPro). 2017. -
A Smart Home is No Castle: Privacy Vulnerabilities of Encrypted IoT Traffic
kNoah Apthorpe, Dillon Reisman, Nick Feamster.
Data and Algorithmic Transparency Workshop (DAT). 2016.




